
Information Security Policy – October 24, 2016
Page 1 of 6
INFORMATION SECURITY POLICY
Policy Type:
Management
Initially
Approved:
October 24,
2016
Policy
Sponsor:
VP, Finance and
Administration
Last
Revised:
October 24,
2016
Primary
Contact:
Information
Technology
Services
Review
Scheduled:
May 1, 2025
Approver:
Board of Governors
A.
OVERVIEW
The intent of this Policy is to set expectations for implementing reasonable safeguards to mitigate
Information loss such as unauthorized or inappropriate access, collection, destruction, use,
modification or disclosure of Information. Unauthorized or inappropriate disclosure of Information
includes unlawful disclosure of information, specifically payment card and personal information.
The University recognizes the need for safe and secure management of Information generated,
collected, accessed, modified, synthesized or maintained to conduct University Operations.
B.
PURPOSE
The purpose of this Policy is to:
1. Prevent unlawful disclosure of information and to comply with Payment Card Industry (PCI)
requirements;
2. Prevent unlawful disclosure of information and to comply with Freedom of Information and
Protection of Privacy (FOIP) Act requirements; and
3. Outlie and communicate expectation and Information Security and Security Controls at the
University.
C.
SCOPE
This Policy applies to all Employees and Users.
D.
POLICY STATEMENT
1.
GENERAL
1.1
Information Security is necessary to maintain uncompromised, reliable Information
that is accessible where and when it is needed for maintaining University
operations.

Information Security Policy – October 24, 2016
Page 2 of 6
1.2
Information Security is characterized by the protection of Information by reasonable
security safeguards against such risks as loss, unauthorized or in appropriate
access, destruction, use, modification, or disclosure of Information.
1.3
Information Security involves more than developing a Security Control such as anti-
malware software. This Policy provides a means to identify and co-ordinate the
University’s approach for maintaining Information Security and Security Controls.
1.4
The University will assign heads of Functional Units to work with ITS to maintain
Critical Technologies using Security Controls.
2.
RESPONSIBILITIES
2.1
Users are responsible for:
a. Reading, complying and acting in accordance with this Policy and any
associated Procedures;
b. Ensuring that any sharing of Information is only to the intended recipient and
the recipient is made aware that the Information is not to be distributed;
c. Ensuring that any non-University systems used to store Information meet
Security Controls;
d. Ensuring that any exchange of Information is compliant with relevant law; and
e. Completing Information Security Awareness Training in compliance with PCI
requirements.
2.2
Management Employees are responsible for:
a. Ensuring that their Employees, and any other relevant Users, are aware of and
act in accordance with this Policy and any associated Procedures;
b. Ensuring that their Employees, and any other relevant Users, are assigned
access only to Information that is necessary to perform the requirements of
their Role; and
c. Ensuring that Information Security Awareness Training has been completed
upon hire and annually by relevant Users in compliance with PCI requirements.
2.3
ITS is responsible for:
a. Identifying, evaluating, documenting and managing Information Security risks
which are identified in the scope of ITS operations or by the University’s risk
management process,
b. Recording, assessing and monitoring attempted and/or actual Information
security breaches with the intent to prevent recurrent;
c. Ensuring that critical or sensitive Information is stored in facilities with secured
areas, physically protected from access, damage, interference and/or theft;
d. Identifying Security Controls in consultation with applicable Functional Units
prior to the development or enhancement of applications and other systems

Information Security Policy – October 24, 2016
Page 3 of 6
that may affect University operations or result in a Technical Landscape
change;
e. Responding to actual or predicted changes to the University’s operational
environment that may affect or result in a Technical Landscape change;
f. Providing guidance, operation support, maintaining, and managing change to
the University’s Technical Landscape to ensure consistency and accuracy in a
timely and cost-effective manner; and
g. Maintaining and administering Information Security Awareness Training in
compliance with PCI requirements on an annual basis.
3.
INFORMATION SECURITY REQUIREMENTS
3.1
Information Security requirements will be identified by ITS in consultation with
applicable Functional Units, prior to the development or enhancement of
applications and other systems that may affect the Technical Landscape.
3.2
The Functional Unit will consult with ITS to assess whether any new technology,
upgrade or maintenance has the potential to affect Information Security or the
Technical Landscape and to apply ITS approved Security Controls.
3.3
The Functional Unit will consult with ITS in order to assess the impact of any
system malfunction or abnormality to ensure that it has not affected Information
Security or the Technical Landscape.
3.4
ITS may require the Functional Unit to provide access to Critical Technologies in
order to assess the impact of any malfunction or abnormality to ensure that it has
not affected Information Security or the Technical Landscape.
3.5
Any Information Security breaches will be thoroughly reviewed and evaluated on a
case by case basis and a full report on the outcomes, causes and findings will be
documented and corrective actions will be implemented, as required.
4.
ACCESS TO INFORMATION
4.1
Access to Information will be limited by the User’s Role within or for the University.
4.2
The University will regularly monitor and control access to Information
requirements to ensure they are current, relevant and that the appropriate level of
access is administered.
5.
SHARING INFORMATION
5.1
Information will not be used or disclosed except where it is needed to conduct
University operations, as provided by this Policy, other University Policies and
Procedures, and relevant law.

Information Security Policy – October 24, 2016
Page 4 of 6
6.
STORAGE OF INFORMATION
6.1
Information will be stored in facilities with secured areas, physically protected from
access, damage, interference and/or theft. These areas will be protected by an ITS
defined security perimeter, specific to each Functional Unit, with enforced security
measures.
6.2
Information will not be stored on non-University secured systems unless the
system meets the same Security Controls.
7.
INFORMATION RETENTION
7.1
Information that has only immediate or short-term operational value to the
University should be considered as transitory and routinely disposed of after the
completion of that particular operational activity or transaction in a secure manner.
7.2
Records that are deemed to have a long-term operational value such as those
containing Information concerning contracts, financial, legal, research or archival
value to the University should be retained according to other University Policies.
8.
INFORMATION SECURITY AWARENESS TRAINING
8.1
The University will administer role-specific training on Information Security upon
hire and annually in compliance with PCI requirements.
9.
COMPLIANCE
9.1
Exchange of Information must comply with this Policy, other applicable Policies and
Procedures, and relevant law.
9.2
Functional Units and Users who act in good faith and execute their responsibilities
with a reasonable standard of care will not be subject to disciplinary action in the
event of an Information Security breach.
E.
DEFINITIONS
(1)
Availability:
ensuring that authorized Users have access to the necessary
Information and associated assets when required
(2)
CIO:
the University’s Chief Information Officer
(3)
Confidentiality:
ensuring that Information is accessible only to those persons
with authorized access
(4)
Critical
Technologies:
these are defined as University systems used for regular
operations, as identified by ITS in consultation with Functional
Units
(5)
Employees:
means individuals who are engaged to work for the University
under an employment contract, including but not limited to
faculty, staff, exempt, casual and management employees

Information Security Policy – October 24, 2016
Page 5 of 6
(6)
Functional Unit:
any division, department, office, program, or other collective
entity of the University
(7)
Information:
specific to this Policy, is personal information and
transactional data in all tangible forms (physical or electronic)
that is collected, maintained, accessed, modified or
synthesized to perform the operations of the University
(8)
Information
Security:
the preservation of Confidentiality, Integrity, and Availability of
Information
(9)
Integrity:
safeguarding the accuracy and completeness of Information
and processing methods
(10)
ITS:
the University’s Information Technology Services Department
(11)
ELT:
the University’s Executive Leadership Team
(12)
PDP:
the University’s Policy Development Plan/Process
(13)
Role:
the behaviours and responsibilities associated with the work
being carried out by an individual for the University
(14)
Secured Areas:
areas intended to physically protect information from access,
damage, interference and/or theft. These areas are
determined by and specific to the needs of the Functional Unit
(15)
Security Controls:
measures in place to safeguard both the Integrity of the
security mechanisms established by ITS and the Technical
Landscape and that are also compliant with this Policy and
relevant law. Security Controls include Users practicing
reasonable standards of care to ensure malicious software
prevention such as checking the authenticity of email
attachments or software installations
(16)
Technical
Landscape:
the set of hardware, software and facility elements, arranged
in a specific configuration, which serves as a fabric to support
the operations of the University
(17)
User:
all individuals dealing with Information. This includes, but is
not limited to, Employees, students, contractors, agents,
consultants, vendors, visitors, volunteers and third parties who
maintain, receive, create, disseminate or use Information
F.
RELATED POLICIES
•
Acceptable Use of Computing and Communication Resources
•
Cash and Payments Handling Policy
•
Email Policy
•
Internet and Network Access
•
Management of Microcomputer Software
•
Records and Information Management Program
•
Enterprise Risk Management Policy
Information Security Policy – October 24, 2016
Page 6 of 6
G.
RELATED LEGISLATION
•
Freedom of Information and Protection of Privacy Act, RSA 2000, c F-25 (FOIP Act)
H.
RELATED DOCUMENTS
•
Data Security Standard version 3.2.1 (May 2018); PCI Security Standards Council
I.
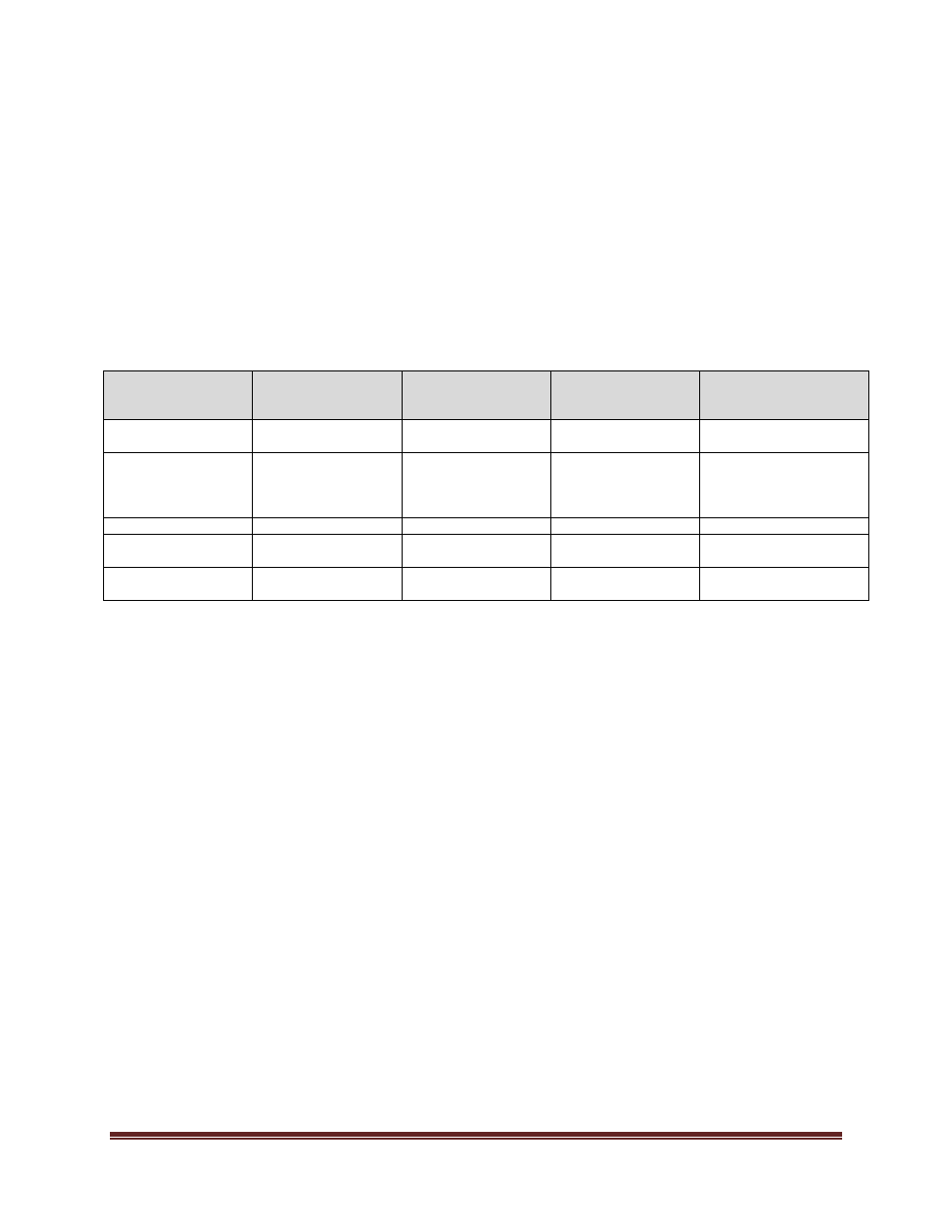
REVISION HISTORY
Date
(mm/dd/yyyy)
Description of
Change
Sections
Person who
Entered Revision
(Position Title)
Person who
Authorized Revision
(Position Title)
10/24/2016
NEW
Director, University
Secretariat
VP, Administrative
Services
07/24/2018
Editorial – Update
Sponsor Title and
Data Security
Standard Version
Policy Specialist
Director, University
Secretariat
01/22/2020
Editorial
Template Update
Policy Specialist
University Secretary
01/19/2022
Editorial
Related Policies
Policy Advisor
General Counsel and
University Secretary
04/20/2023
Editorial
Definitions
Policy Advisor
General Counsel and
University Secretary
Document Outline





