
Email Policy – February 10, 2014
Page 1 of 5
EMAIL POLICY
Policy Type:
Management
Initially
Approved:
December
2013
Policy
Sponsor:
VP, Finance &
Administration
Last
Revised:
February 10,
2014
Primary
Contact:
CIO and AVP, IT
Services
Review
Scheduled:
May 1, 2025
Approver:
Board of Governors
A.
OVERVIEW
The University email system is a vital part of the University's information technology services. It is
a service provided to support communication in conducting and administering the business of the
University, including teaching, research, and scholarly activities.
B.
PURPOSE
The purpose of this Policy is to define the acceptable use and outline responsibilities of usage of
University email.
C.
SCOPE
Compliance with University Policies and Procedures extends to all members of the University
community.
This Policy applies to faculty, staff, students, retirees, alumni and other parties that have been
provided a University assigned email account.
D.
POLICY STATEMENT
1.
GENERAL
1.1
The University provides an email account to all faculty, staff and students to be
used in the course of their duties or activities at the University. The University may
also provide an email account for alumni, retirees, and professor emeriti, as well
as other at the discretion of the University. These accounts are signified by a
@mtroyal.ca or @mymru.ca.
1.2
All email accounts and associated addresses are the property of the
University.
1.3
Employees and other parties are required to use their @mtroyal.ca email account
for communication, correspondence and business related to their duties or
activities with Mount Royal University.

Email Policy – February 10, 2014
Page 2 of 5
1.4
The @mtroyal.ca/@mymru.ca email account will be considered the individual's
official University email address. It is the responsibility of the account holder to
ensure that email received as their official University address is dealt with in a
timely manner.
1.5
Most email is created for routine or information exchange. Email records that have
only immediate or short-term value to the University should be considered as
transitory and routinely disposed of after the completion of that particular business
activity or transaction in a secure manner.
1.6 Email records that are deemed to have a long term value such as those containing
information concerning contracts, financial, legal, research or archival value to the
University should be retained according to the Records and Information
Management Program policy.
2.
RESPONSIBILITIES OF USERS
2.1
All users must conduct email exchanges with professionalism and courtesy and
manage their email responsibly.
2.2
Employees and other parties should make every effort to use their @mtroyal.ca
address for only work related correspondence. Personal correspondence should
be conducted with an individual's personal email address.
2.3
Users shall ensure that they use and manage their University email in accordance
with the following policies:
a) Access to Information Policy
b) Code of Student Conduct
c) Human Rights Policy
d) Information Management Policy
e) Mount Royal Computing Resources Acceptable Use Policy
f) Personal Harassment Policy
g) Records and Information Management Program Policy
h) Security and Responsible Use of Computing and Network
Resources Policy
i) Use of Copyrighted Materials Policy
2.4
It is the account holder's responsibility to properly store all email messages or
attachments that are required for ongoing use and to securely dispose of any email
message that is no longer required. In the event of an access to information
request under the Freedom of Information and Protection of Privacy Act, there may
be a Legal Hold on any applicable email records contained in the user's account.
It is the account holder's responsibility to not delete email records at any time until
the University has responded to the access request in accordance with provincial
privacy legislation. Users should refer to the Freedom of Information and
Protection of Privacy Act or the University's FOIP Office for further information
regarding email and privacy issues.
2.5
Email forwarding and access is done at account holder's own risk and
responsibility.
2.6
In using email, users must comply with all applicable federal and provincial laws
and all applicable University rules and policies. Rules and policies include, but are
not limited to, the laws relating to privacy, copyright, obscenity, libel and child

Email Policy – February 10, 2014
Page 3 of 5
pornography; the University's Code of Student Conduct, the University's Personal
Harassment Policy and the University's Human Rights Policy. Users who engage
in communications with persons in other geographic areas should be aware that
they may also be subject to laws of those other jurisdictions.
2.7
Unencrypted email is not a secure method for transmitting confidential information
or sensitive data over the Internet. If it is necessary to send such information,
users must take steps to secure it by encrypting your message, taking into account
the sensitivity of the data being transmitted and the level of security at the source
and destination systems.
2.8
Email account holders may use their email for incidental personal purposes
provided that such use does not:
a) Directly or indirectly interfere with the operation of computing facilities or
email services.
b) Burden the University with noticeable incremental cost.
c) Interfere with the email holder's employment or other obligation to the
University.
d) Contravene this or any other University Policy.
e) Facilitate a private commercial activity.
f) Spamming, chain letters, unauthorized unsolicited email and
Phishing are prohibited.
g) Email records arising from personal use may be subject to access by the
University as described in the Access and Privacy section of this Policy.
Users should assess the implications of the Access and Privacy section of
this Policy in deciding whether to use University email services for personal
purposes.
3.
RESPONSIBILITIES OF SERVICE PROVIDERS
3.1
Email accounts provided by the University are institutional property, and those
responsible for maintaining these services are responsible for ensuring that
institutional standards are appropriately applied. However, the security and
confidentiality of email cannot be guaranteed. Also, providers of email services
have no control over the security of email that has been downloaded to a user's
computer. Users are responsible for employing protections (e.g., strong
passwords) that are available to them as a deterrent to potential intruders and the
misuse of email.
3.2
Searchable electronic address directories - some public, some private may be
maintained and populated from the email addresses provided by the University.
The content of such email address directories are institutional data. Faculty and
staff may, in special circumstances, request to Human Resources not to be
included in public directories.
3.3
The University reserves the right to reject any email that could compromise the
University network and any systems connected to it. Information Technology
Services (ITS) will ensure reasonable processes are in place to deal with email
containing viruses, to reject email from known Spam sites, and to scan incoming
email for Spam, but the University cannot guarantee the success of such
processes. Users must accept the risk inherent in the use of technology.

Email Policy – February 10, 2014
Page 4 of 5
3.4
Email is backed up for purpose of disaster recovery only and not for recovery of
specific items of deleted email or other requests. Users are responsible for
backing up any email they require for ongoing purposes.
3.5
The University is not responsible or libel for the content created, sent, forwarded,
contained or stored in an email account.
4.
ACCESS AND PRIVACY
4.1
The confidentiality of user's email may be compromised by the applicability of
labour policy, by unintended redistribution, because of legal requirements such as
disclosure obligations, or because of the inability of current technologies to protect
against unauthorized access. Users are expected to and must exercise extreme
caution in using email to communicate confidential or sensitive matters.
4.2
The University reserves the right to access email records, including those which
have been deleted by the account holder. In addition, the University reserves the
right to access email records where there are reasonable grounds to believe that
those records contain information necessary to the proper functioning of the
University's business.
4.3
Wherever practical, users will be notified promptly when their email records have
been accessed by the University.
4.4
In the event of an access to information request under the Freedom of Information
and Protection of Privacy Act, the University's FOIP Office will make every
reasonable effort to present a formal notification to the required user. The
University reserves the right to not provide notification if there are reasonable
grounds to believe that the notification would affect the proper functioning of
University business.
E.
DEFINITIONS
(1)
Phishing:
is the act of attempting to acquire information such as user
names, passwords, and credit card details (and sometimes,
indirectly, money) by masquerading as a trustworthy entity in
an electronic communication.
(2)
Spam/Spamming:
Spam includes electronic junk mail or junk newsgroup
postings, and generally Spam is any unsolicited email
(3)
University:
means Mount Royal University
F.
RELATED POLICIES
•
Access to Information Policy
•
Code of Student Conduct
•
Human Rights Policy
•
Information Security Policy
•
Records and Information Management Program Policy
•
Workplace Violence and Harassment Policy
Email Policy – February 10, 2014
Page 5 of 5
G.
RELATED LEGISLATION
•
Alberta Freedom of Information and Protection of Privacy Act – Revised Statutes of
Alberta, 2000, Chapter F-24 with amendments in force as of July 1, 2012.
•
Alberta Freedom of Information and Protection of Privacy Regulation –
Alberta
Regulation 186/2008 with amendments up to Alberta Regulation 31/2012.
a) Alberta Human Rights Act – Revised Statutes of Canada, 2000, A-25.5 with
amendments in force as of November 1, 2010.
b) Canada Copyright Act –
Revised Statutes of Canada, 1985, Chapter C-42 with
amendments in force November 27, 2012.
H.
RELATED DOCUMENTS
•
Government of Alberta Official and Transitory Records: A Guide for the
•
Government of Alberta, November 2011.
•
International Organization for Standardization (ISO) 15489, Information and Documentation –
Records Management, 2001. References.
I.
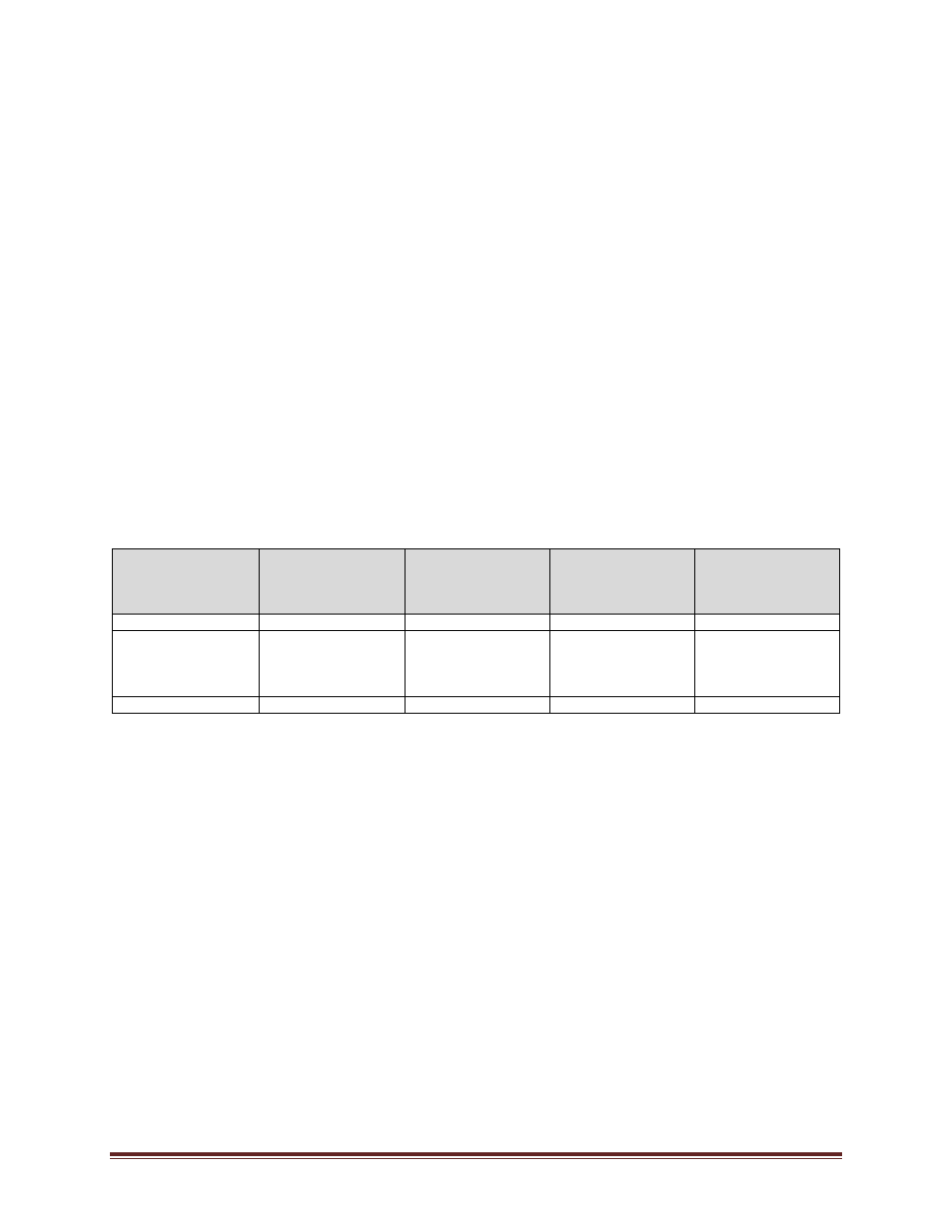
REVISION HISTORY
Date
(mm/dd/yyyy)
Description of
Change
Sections
Person who
Entered Revision
(Position Title)
Person who
Authorized
Revision
(Position Title)
02/10/2014
NEW
08/31/2017
Editiorial –
conversation to new
template; title
changes
University Secretary
01/22/2020
Editorial
Template Update
Policy Specialist
University Secretary




