
Procedure for Managing a Privacy Breach
– June 11, 2021
Page 1 of 5
PROCEDURE FOR MANAGING A PRIVACY
BREACH
Procedure
Type:
Management
Initially
Approved:
June 11,
2021
Procedure
Sponsor:
General Counsel
and University
Secretary
Last Revised:
Primary
Contact:
Information
Management &
Privacy Office
Review
Scheduled:
June 11,
2026
Approver:
Executive Leadership Team
A.
PROCEDURES
1.
REPORTING A PRIVACY BREACH
1.1
A privacy breach occurs when there is unauthorized access to or collection, use,
disclosure, or disposal of Personal Information.
1.2
An individual may seek advice from the Information Management & Privacy Advisor
(“IMPA”) in advance of submitting a Privacy Breach Report or where immediate steps
are needed to address an ongoing breach. The Information Management & Privacy
Advisor can be contacted at
foip@mtroyal.ca
.
1.3
If an Employee believes that there has been a privacy breach, they must submit a
Privacy Breach Report to the University FOIP Office and notify their supervisor.
1.4
If an individual believes that there has been a breach of their own Personal
Information, they may submit a Privacy Breach Report to the University
’s FOIP
Office.
1.5
Any individual may also report a privacy breach directly to the Commissioner.
2.
RECEIPT OF A PRIVACY BREACH REPORT
2.1
Upon receipt of a Privacy Breach Report, the IMPA will investigate the alleged
privacy breach to determine what further action is required.
2.2
When a privacy breach has been confirmed, the IMPA will:
a. work with the impacted Unit(s) to identify steps needed to contain the breach;
b. ensure that the University provides any applicable notification to the impacted
individual(s) and the Commissioner; and
c. assess the processes safeguarding the Personal Information subjected to the
privacy breach, in consultation with the impacted Unit(s).

Procedure for Managing a Privacy Breach
– June 11, 2021
Page 2 of 5
2.3
If the IMPA determines that no privacy breach has occurred, they will notify the
submitter of the Privacy Breach Report that no privacy breach has occurred, and no
further action will be taken.
3.
CONTAINING A PRIVACY BREACH
3.1
The IMPA will notify, as applicable, any impacted Units, relevant subject matter
experts, or third parties of a confirmed privacy breach.
3.2
The IMPA, impacted Units, and subject matter experts are expected to consult and
coordinate the institutional response to a privacy breach.
3.3
The impacted Unit(s) will:
a. recover, retrieve, or destroy any Records or otherwise take steps to contain the
privacy breach;
b. limit access to key file management or software systems (e.g. change
passwords, access, identification numbers, or shut down system); and
c. assess security protocols concerning the breach and implement interim solutions
for any immediate process weaknesses (physical, technical, administrative).
4.
NOTIFICATION OF THE PRIVACY BREACH
4.1
Notification is assessed on a case-by-case basis and the key consideration is the
avoidance or mitigation of harm to an individual whose privacy has been breached.
The IMPA will determine when a notice, including its contents, will be sent to an
individual whose privacy has been breached.
4.2
The IMPA will work with the Unit(s) involved to decide the best approach for
notification.
4.3
Notification of individuals affected by a privacy breach will occur as soon as is
reasonable following the privacy breach. However, if law enforcement authorities
are involved, the IMPA will consult with those authorities to determine whether
notification should be delayed in order not to impede a criminal investigation.
4.4
The notification will include:
a. date and description of the privacy breach;
b. description of the information inappropriately accessed, collected, used, or
disclosed;
c. the steps taken to mitigate the harm;
d. next steps planned and any long-term plans to prevent future breaches;
e. steps the individual can take to further mitigate the risk of harm;
f.
The contact information of the IMPA; and
g. the contact information for the Office of the Commissioner.

Procedure for Managing a Privacy Breach
– June 11, 2021
Page 3 of 5
4.5
The IMPA may also decide to report the privacy breach to the Commissioner
depending on the overall evaluation of the privacy breach, based on the following
factors:
a. whether the disclosed Personal Information has been, or will be, used to commit
identity theft or other harm;
b. the sensitivity of the Personal Information disclosed;
c. the severity or harm to individuals from the privacy breach;
d. the number of people affected by the privacy breach; or
e. the Personal Information has not been fully recovered.
5.
PRIVACY BREACH REVIEW
5.1
Once the immediate steps to contain a privacy breach have been completed, the
IMPA will review and assess the privacy breach to determine:
a. the circumstances giving rise to the privacy breach.
b. the number of individuals impacted, the sensitivity of the Personal Information,
and the potential for harm.
c. the safeguards in place prior to the privacy breach.
d. the effectiveness of the steps taken to contain the privacy breach.
e. any immediate, ongoing, and foreseeable risks concerned with Personal
Information in the Unit.
f.
recommendations to prevent a future privacy breach (e.g. privacy training,
security process, technical improvements, policy or process review).
5.2
The above recommendations will be presented to the Unit Head responsible for the
respective Unit concerning the breach.
5.3
The IMPA and the Unit Head will work together to ensure that the necessary changes
are implemented so that a similar privacy breach will not occur again in the future.
5.4
The IMPA will submit a report annually to the Office of General Counsel as part of
the legislative compliance process, and will include:
a. the number of reported privacy breaches;
b. the circumstances surrounding the privacy breach;
c. any action taken resulting from the privacy breach, or, if actions were not taken,
the reasons why no actions were taken.

Procedure for Managing a Privacy Breach
– June 11, 2021
Page 4 of 5
B.
DEFINITIONS
(1)
Commissioner:
means the Information and Privacy Commissioner of
Alberta appointed in accordance with the Act
(2)
Employee:
means individuals who are engaged to work for the
University under an employment contract, including but
not limited to faculty, staff, exempt, casual and
management employees
(3)
IMPA:
means the University’s Information Management &
Privacy Advisor
(4)
Personal Information:
means recorded information about an identifiable
individual, including:
a.
the individual’s name, home or business
address or home or business telephone
number,
b.
the individual’s race, national or ethnic origin,
colour or religious or political beliefs or
associations,
c.
the individual’s age, sex, marital status or family
status,
d. an identifying number, symbol or other
particular assigned to the individual,
e.
the individual’s fingerprints, other biometric
information, blood type, genetic information or
inheritable characteristics,
f.
information a
bout the individual’s health and
health care history, including information about
a physical or mental disability,
g.
information about the individual’s educational,
financial, employment or criminal history,
including criminal records where a pardon has
been given,
h.
anyone else’s opinions about the individual, and
i.
the individual’s personal views or opinions,
except if they are about someone else.
(5)
Policy:
means the Privacy policy
(6)
Record:
means a record of information in any form and includes,
but is not limited to, notes, emails, letters, images,
audiovisual recordings, documents, maps, drawings,
photographs, letters, invoices, and any other information
that is written, photographed, recorded, captured, or
stored in any manner. Notably, the definition does not
Procedure for Managing a Privacy Breach
– June 11, 2021
Page 5 of 5
include software or any mechanism that produces or
reads records.
(7)
Unit:
means an academic or business Unit of the University
(8)
Unit Head:
means Deans, Department Heads, Division Heads,
Directors, Executive Directors, University Registrar, and
other senior administrators at a comparable level; and
Associate Vice-Presidents, Vice-Presidents, and the
President, as applicable.
(9)
University:
means Mount Royal University
C.
RELATED POLICIES
• Access to Information policy
• Information Security policy
• Privacy policy
D.
RELATED LEGISLATION
• Freedom of Information and Protection of Privacy Act, RSA, 2000, c F-25
E.
RELATED DOCUMENTS
• Privacy Breach Report Form
F.
REVISION HISTORY
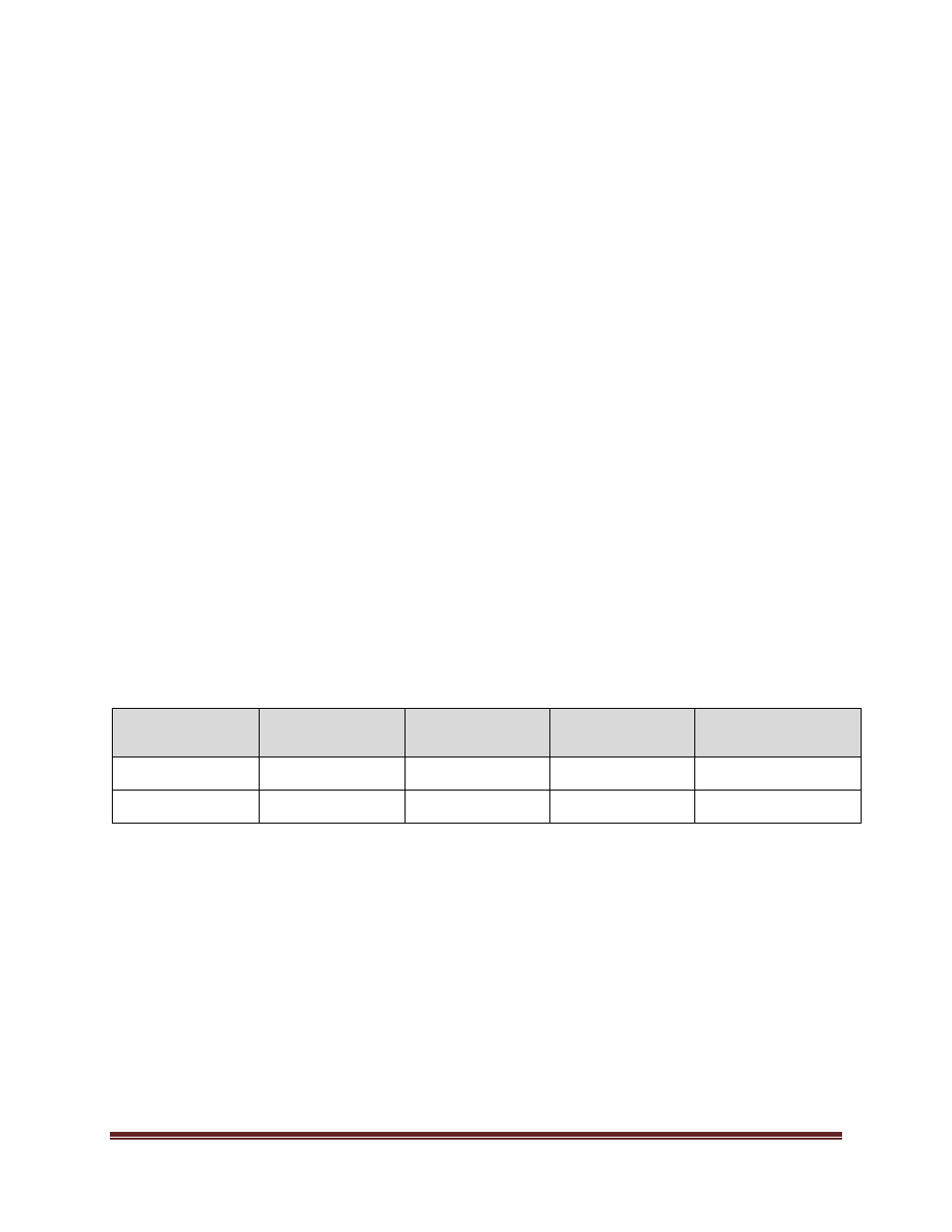
Date
(mm/dd/yyyy)
Description of
Change
Sections
Person who
Entered Revision
(Position Title)
Person who
Authorized Revision
(Position Title)
01/19/2022
Editorial
Related Policies
Policy Advisor
General Counsel and
University Secretary
04/20/2023
Editorial
Definitions
Policy Advisor
General Counsel and
University Secretary




